The Department of War has launched the Cybersecurity Risk Management Construct (CSRMC) to improve enterprise-wide cybersecurity governance. This new approach moves beyond compliance checklists and focuses on continuous, integrated risk management, making cybersecurity faster, smarter, and mission-aligned.
How CSRMC Enhances Governance
CSRMC provides a structured, five-phase lifecycle:
Design → Build → Test → Onboard → Operate
This lifecycle ensures cybersecurity is embedded from the start and maintained through real-time monitoring and governance dashboards. Instead of isolated risk decisions, CSRMC creates enterprise-level visibility and accountability, aligning cybersecurity priorities with operational goals like mission readiness and mission resilience under cyber-contested conditions.
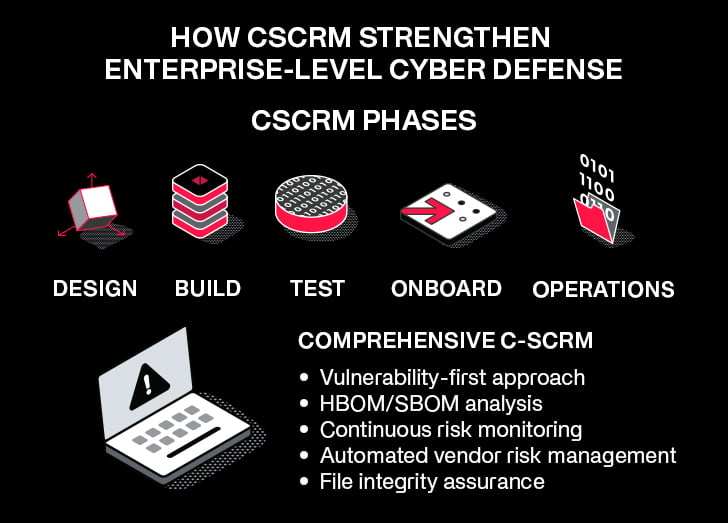
Why Comprehensive C-SCRM is Critical for Cybersecurity Risk Management Construct
Cybersecurity governance doesn’t stop at your network. Adversaries look to exploit vulnerabilities in the entire supply chain through vendors, hardware and software. Without comprehensive and continuous Cyber Supply Chain Management even the best governance framework can fail.
C-SCRM ensures:
-
Visibility into supplier risks before they impact mission-critical systems
-
HBOM/SBOM analysis to detect vulnerabilities in hardware and software
-
Continuous monitoring across procurement and sustainment cycles
Together, CSRMC and C-SCRM create a complete defense strategy that governs risk at the enterprise level while securing the supply chain underpinning every system.
Fortress Government Solutions: Proven C-SCRM Tools
Fortress Government Solutions offers comprehensive C-SCRM solutions that directly support CSRMC implementation:
-
Mission-focused risk prioritization approach to secure systems throughout the entire lifecycle
-
Hardware and Software provenance and risk illumination, prioritization and management
-
AI enhanced Automated Vendor Risk Management
-
SBOM analysis and continuous monitoring
These tools deliver risk illumination, remediation recommendations, continuous risk monitoring, automated vendor assessments utilizing AI, and provide near-real time risk data for mission focused risk prioritization in addition to compliance mapping to NIST and DOW standards.
Action Checklist
-
Integrate CSRMC early in design and acquisition.
-
Secure the supply chain with Vendor, SBOM/HBOM analysis.
-
Adopt continuous monitoring—move beyond static approvals.
-
Use proven, enterprise level C-SCRM Platforms like Fortress to secure your most critical systems.
Bottom line: CSRMC strengthens enterprise-wide governance by embedding cybersecurity into every phase of system development and operation. Comprehensive C-SCRM ensures that governance extends beyond the network to the entire supply chain—making both essential for mission readiness and execution.