-
-
Platform
-
Company
-
-
-
Commercial
- Industry Collaboration
- Solutions
- Industries
-
© 2025 Fortress Information Security. All rights reserved






North American Energy Software Assurance Database
Analysis of software bill of materials (SBOMs) isn’t just a supplementary measure for proactive product security—it’s essential. Yet, scaling these security workflows can be costly and complex.
Recognized with the 2024 Critical Infrastructure Security Award for its innovation and leadership, NAESAD simplifies these processes, delivering cost-effective, proactive security at scale.
NAESAD brings together critical infrastructure, government entities, and vendors to elevate risk management through accessible product security data for software products. a vast repository of over 15,000 critical bills of materials available on-demand and streamlined workflows for creating and requesting new ones, NAESAD delivers a unified, scalable approach to security.
Organizations utilizing NAESAD gain enhanced protection against exploitation, a stronger security posture, and reduced resource demands.
NAESAD enables procurement professionals, risk and compliance, and security teams to secure their organizations.
Ensure readiness across defense and
government entities.
Achieve visibility across the supply chain
with the latest in cyber risk technology.
Identify vulnerable components for prioritized resolution, reducing costs and focusing on critical areas.
NAESAD enables scalable data sharing allowing vendors to share once increasing efficiency and streamlining data distribution.
Risk Management
Through the Product Lifecycle
NAESAD meets risk requirements of large enterprise organizations throughout the product lifecycle through procurement, risk evaluation, and vulnerability management.


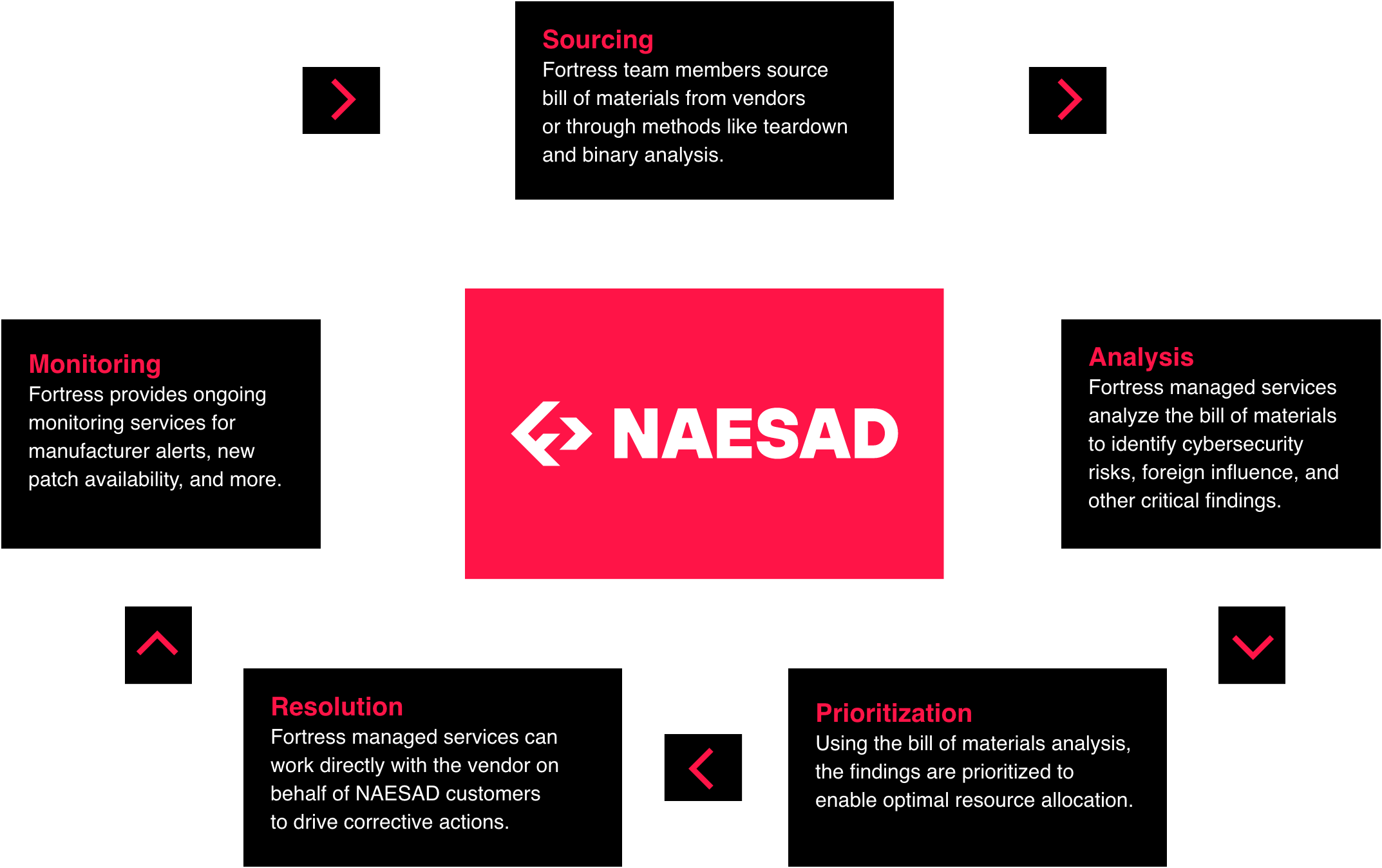
Enhance supply chain security and efficiency with NAESAD, integrating tools and insights for lifecycle resilience and ROI.
15,000+ SBOMs for full lifecycle security
Connects organizations and vendors for joint risk management
The North American Energy Software Assurance Database (NAESAD) improves software and hardware product quality by sharing vetted product assessments industry-wide.