-
-
Platform
-
Company
-
-
-
Commercial
- Industry Collaboration
- Solutions
- Industries
-
© 2025 Fortress Information Security. All rights reserved






In today’s connected world, security and compliance risks can often come from third-party organizations, such as vendors, underscoring the importance of due diligence and continuous monitoring of third-parties. Fortress enables streamlined TPRM capabilities so that customers can quickly detect and resolve risks from vendors across a wide variety of important categories including cybersecurity, FOCI, ESG, and more.
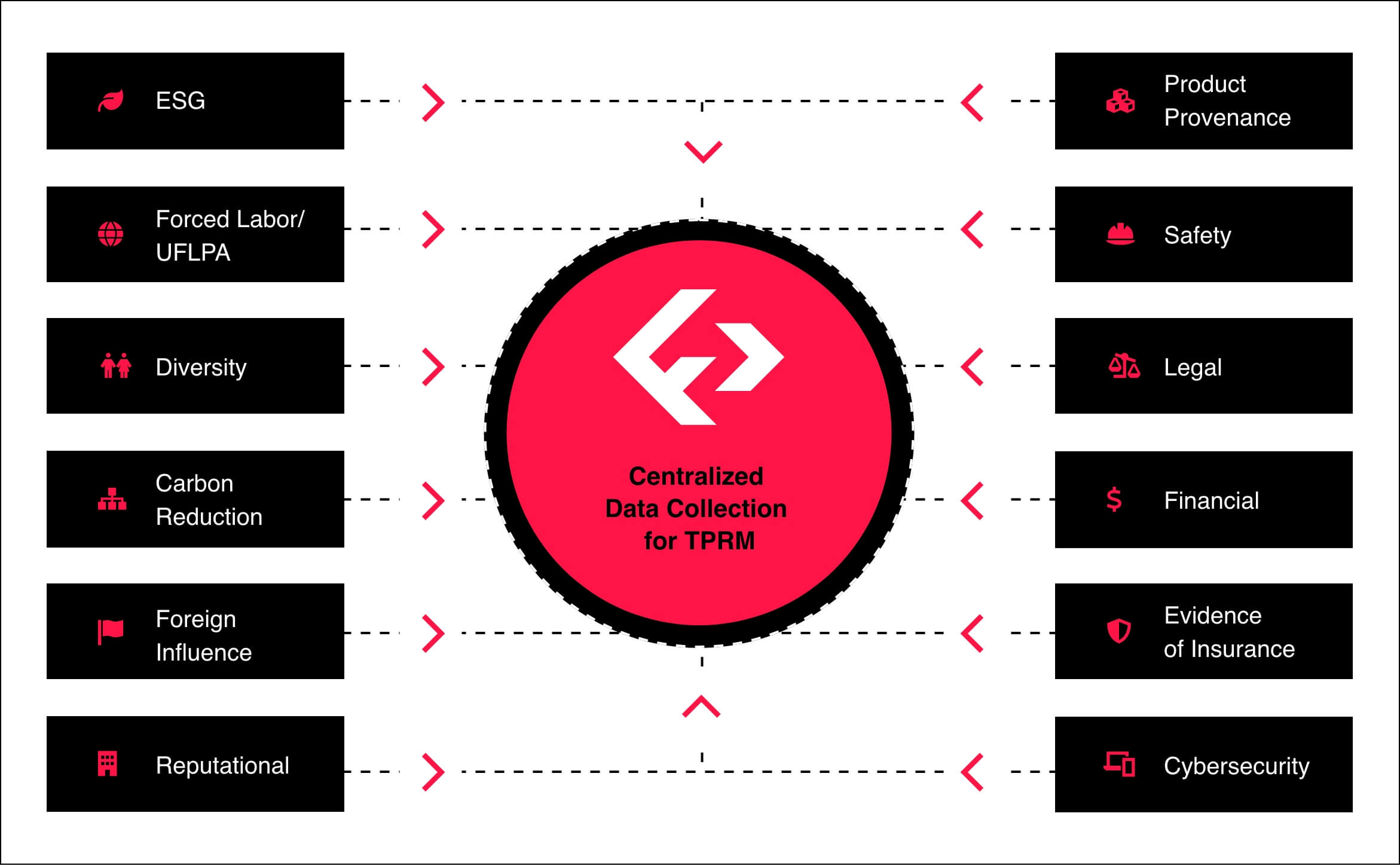
Fortress enables an efficient process for TPRM to quickly and proactively reduce risks created by vendor ecosystems.

Utilizing AI-enhanced tools alongside managed services, Fortress exposes hidden vulnerabilities within third-party vendor operations, ensuring comprehensive risk detection across the vendor ecosystem.

Combining AI, the robust Fortress Platform, and expert managed services, Fortress supports organizations in effectively resolving third-party risks, contributing to the fortification of the supply chain.

Through its vigilant monitoring mechanisms, Fortress continuously monitors third-party vendors for emerging risks, offering timely alerts and enabling proactive risk management within TPRM programs.

Fortress-enabled industry collaboratives collect data artifacts once and enable sharing to multiple customers empowering organizations to rapidly access essential data artifacts quickly and for lower costs resulting in a more robust TPRM program.



Fortress Platform offers broad spectrum coverage of security and compliance risk factors for a 360-degree view of vendors and suppliers improving third-party risk mitigation.
Fortress hosts data exchanges that facilitate the seamless sharing of critical insights between risk management professionals to empower organizations to effectively manage their vendor ecosystems.
Organizations leverage Fortress to get results that drive decision-making to power their third-party risk management strategy and enable a safe and resilient vendor ecosystem.
Your cyber supply chain, encompassing hardware, software, processes, and vendor network, conceals undiscovered potential vulnerabilities.
Engage in our 30-minute discovery assessment to unveil these weaknesses and take proactive measures to mitigate your risk.