-
-
Platform
-
Company
-
-
-
Commercial
- Industry Collaboration
- Solutions
- Industries
-
© 2025 Fortress Information Security. All rights reserved
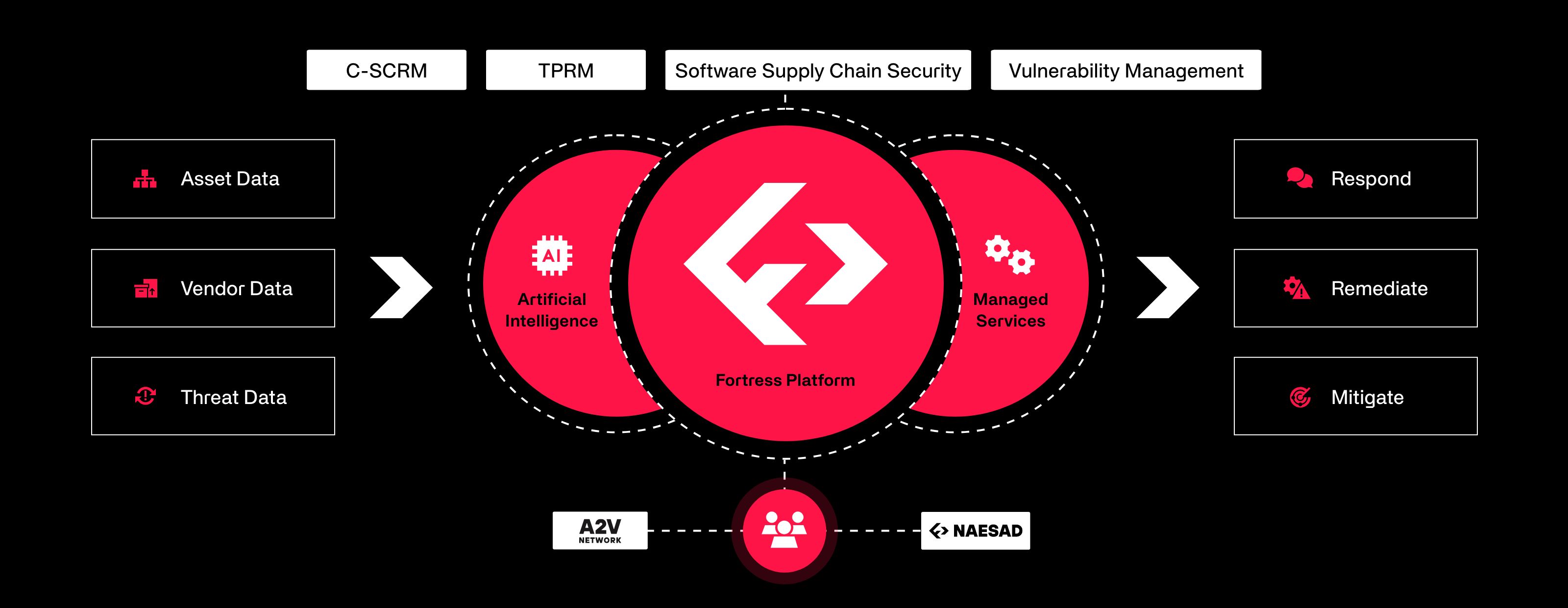
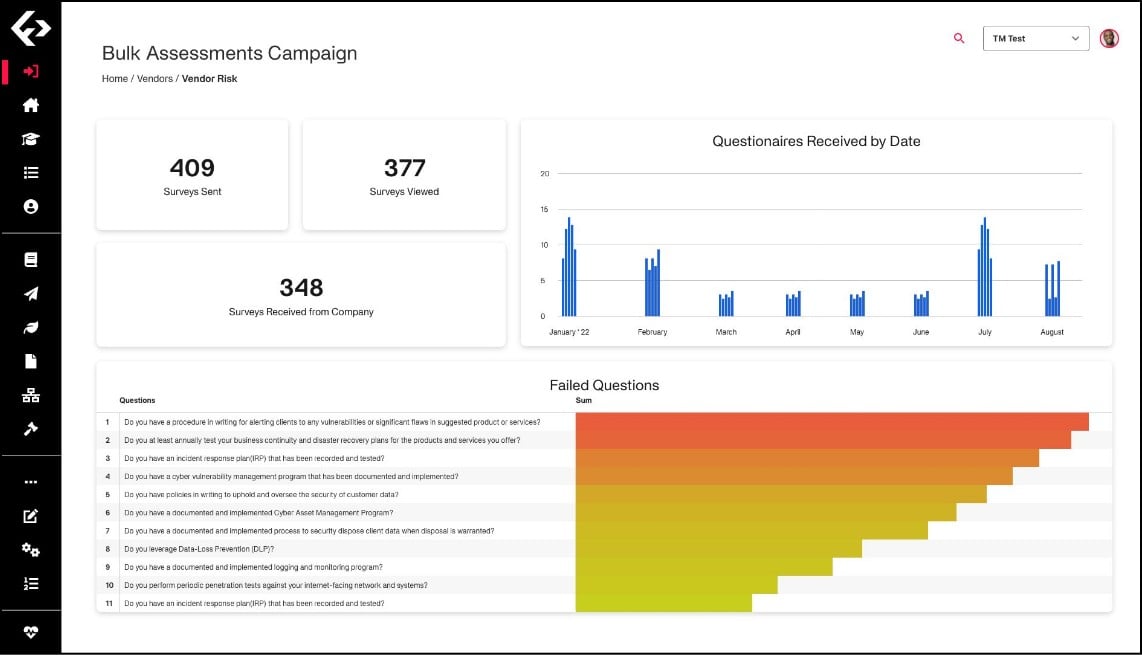

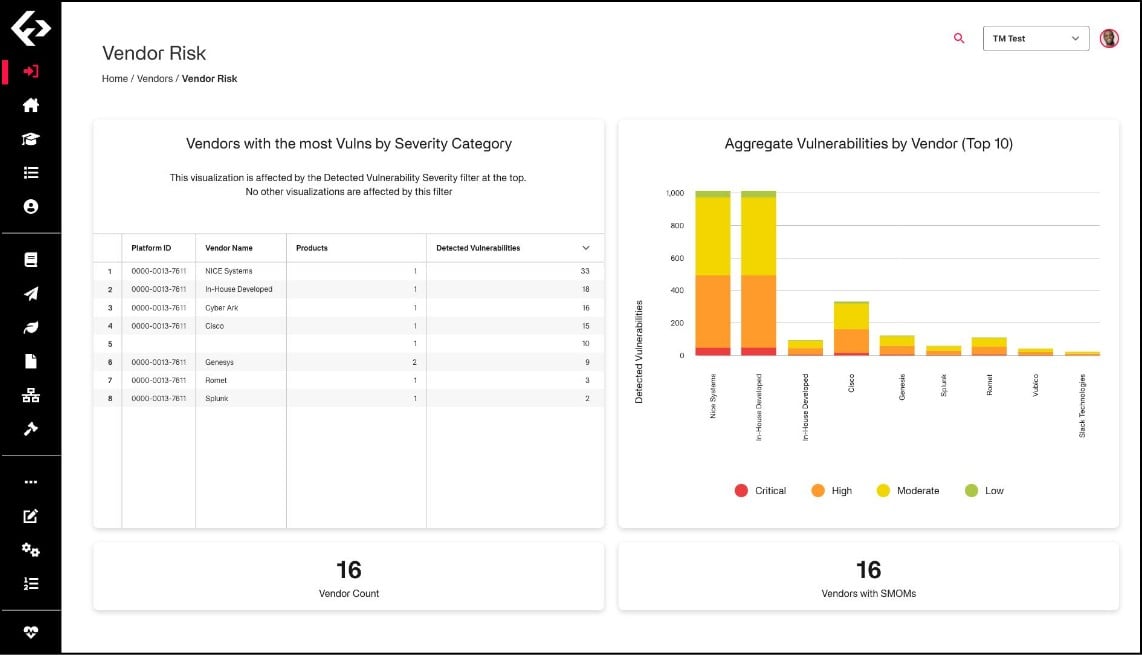

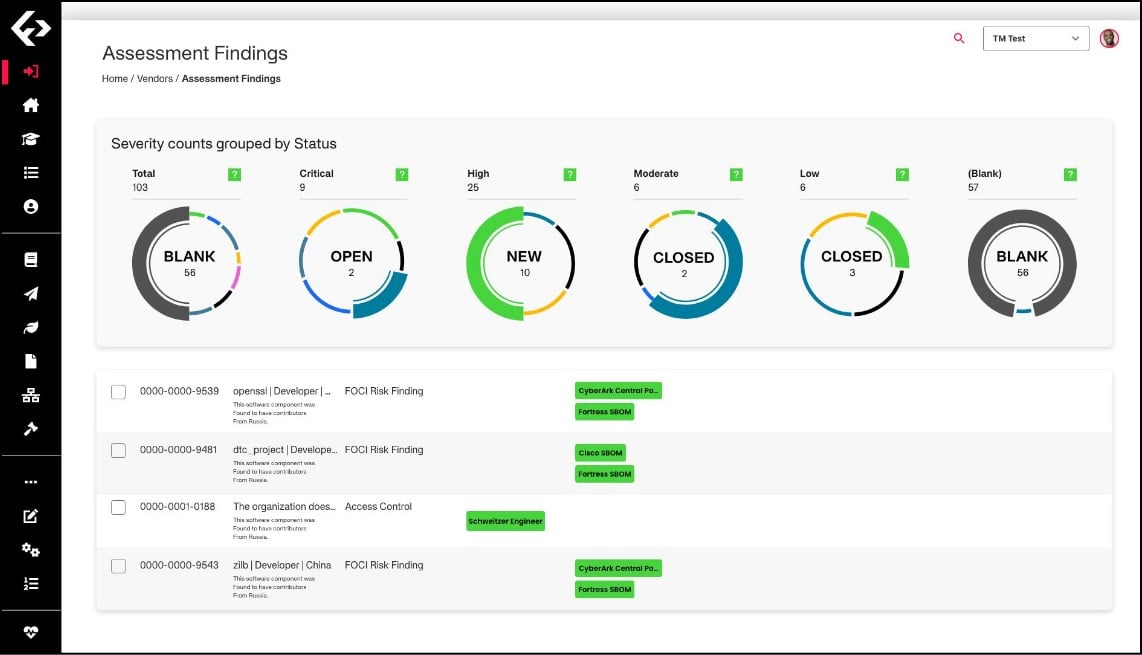

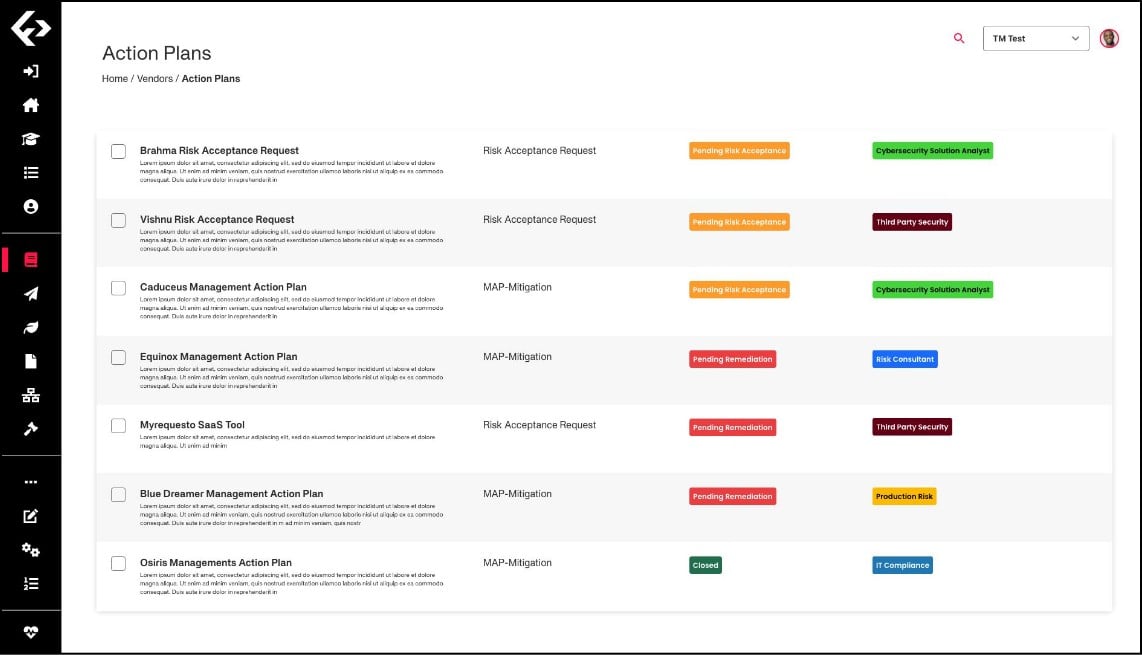

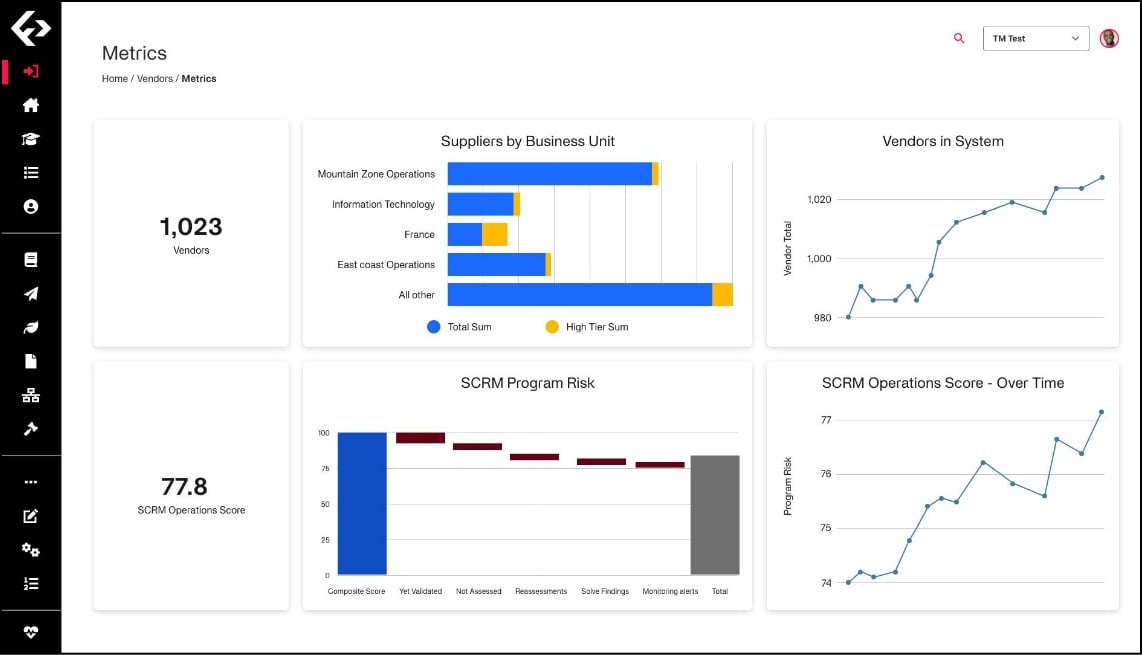

Conclusive Results
Provides customized solutions utilizing sector-specific best practices.
Encourages shared data sourcing for collective risk solving.
Instantly elevates the sophistication of security programs.
Drastically cuts down time to remediate or mitigate vulnerabilities.
What Our Customers Say