-
-
Platform
-
Company
-
-
-
Commercial
- Industry Collaboration
- Solutions
- Industries
-
© 2025 Fortress Information Security. All rights reserved






Fortress’s C-SCRM solution enables a proactive strategy for streamlining the supply chain lifecycle from evaluating procurement and compliance risks to implementing security controls.
Supply chain risk mitigation and vulnerability protection is crucial to ensuring the protection of critical infrastructure industries. Fortress’s comprehensive C-SCRM product set provides conclusive insights and results enabling organizations to evolve the resiliency of their supply chain security.

Fortress detects risk across vendors and assets leveraging AI-powered solutions in combination with managed services to identify hidden cyber risks.

Fortress enables efficient risk resolution by streamlining management through action plan risk tracker and providing timely cyber threat intelligence for rapid incident response.

Fortress provides continuous monitoring for vendors and assets, enabling proactive cybersecurity management and prompt threat detection and notification.

Fortress-enabled industry collaboratives collect data artifacts once and enable sharing to multiple customers empowering organizations to collect essential data artifacts quickly and for lower costs resulting in a more resilient cyber supply chain.



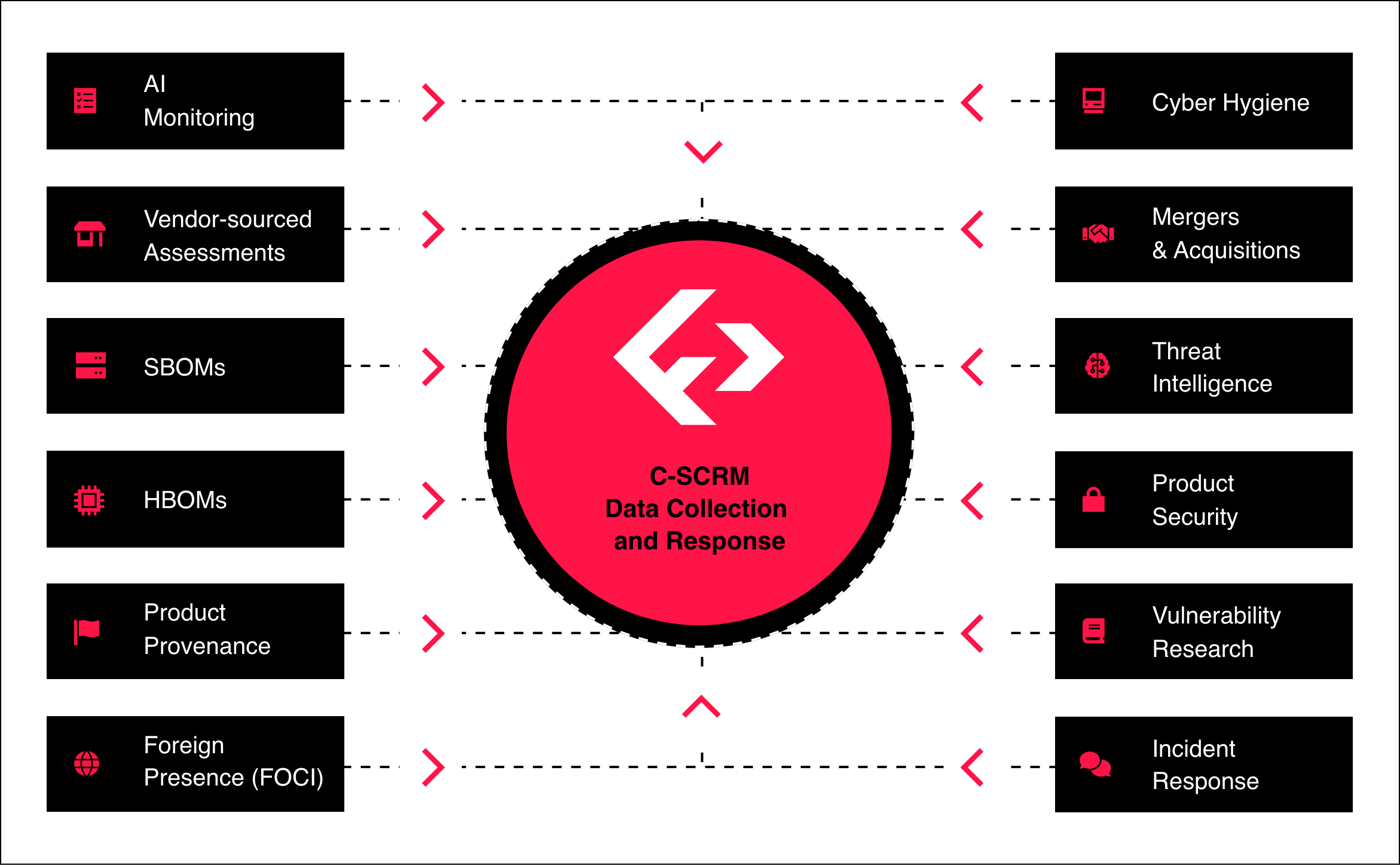
Cyber Supply Chain Risk Management (C-SCRM) identifies and mitigates risks from vendors, hardware, and software. Fortress provides a holistic view to uncover vulnerabilities that traditional tools miss.
Most organizations use fragmented tools for vendors, software, and hardware that don’t integrate. Fortress connects these layers for a unified, prioritized view.
Traditional tools focus on vendor financial or geographic risks. Fortress goes deeper, analyzing software (SBOMs), hardware (HBOMs), and components to catch hidden vulnerabilities.
Fortress is cyber-first, integrative, and flexible. Fortress identifies gaps, integrates existing tools, and delivers workflows to assess, prioritize, and resolve risks.
Organizations get actionable insights, integrated workflows, and ongoing collaboration that strengthen programs and reduce risk over time.